Hackers are attempting to sabotage elections in Europe and have brought American democracy into question. A £1.9 billion investment and a new cyber-security centre proves just how seriously the UK is taking cyber-crime, writes Tom Pattinson
On Valentine’s Day, Queen Elizabeth II and Prince Phillip attended a formal opening in a cavernous, steel and glass building in Victoria, central London. One of the only public appearances the Queen has made this year, the visit was to open the government’s National Cyber Security Centre (NCSC). The centre has been established to combat cybercrime and attacks on government and British businesses, as well as to protect the economy and society at large.
In October 2016, as the NCSC was just starting operations, the sitting head of Mi5, Andrew Parker, gave an interview to a newspaper. In the only interview an incumbent Mi5 chief had given in the organisation’s 107-year history, Parker said that, while much attention was focused on Islamic extremism, cyber terrorism and cybercrime pose a major threat to the UK.
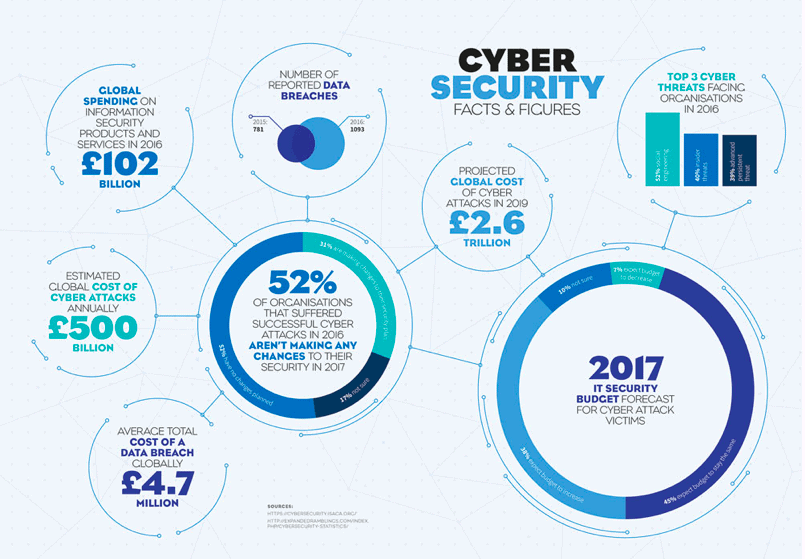
In a speech, in November 2016 Philip Hammond, the UK’s chancellor of the exchequer, said that the UK must “keep up with the scale and pace of the threats we face”. He announced a £1.9 billion package to be spent “proactively attacking those that attack”. That package also helps fund the NCSC and the estimated 50 newly recruited specialists who work there, while more than 100 private sector experts have been seconded to work there, funded by the companies from which they came.
“Government cannot protect business and the general public from the risks of cyber-attack on its own. It has to be a team effort,” said Hammond. “It is only in this way that we can stay one step ahead of the scale and pace of the threat that we face.”
The NCSC is under the purview of GCHQ – the government’s intelligence-gathering centre – and is being headed up by Ciaran Martin, formerly cyber security director of GCHQ. “We will help secure our critical services, lead the response to the most serious incidents and improve the underlying security of the internet through technological improvement and advice to citizens and organisations,” Martin said.
In the three months since opening, the NCSC saw 188 Category Two or Three cyber attacks. The UK has yet to fall victim to a Category One attack, the highest level, such as the theft of confidential details of millions of American government workers in June 2015.
At the February opening of the NCSC Hammond said that “the cyber-attacks we are seeing are increasing in their frequency, their severity, and their sophistication”. And Martin, the centre’s chief executive said that the UK has “had significant losses of personal data, significant intrusions by hostile state actors, significant reconnaissance against critical national infrastructure”.
The centre will protect critical infrastructure, such as energy and transport and create automated defences to safeguard citizens and businesses and deter attacks from criminals and “hostile actors”, said Hammond.
One of those hostile actors, according to Mi5 chief Parker, is Russia. “It is using its whole range of state organs and powers to push its foreign policy abroad in increasingly aggressive ways – involving propaganda, espionage, subversion and cyber-attacks,” he said. “Russia is at work across Europe and in the UK today.”
Parker’s comments were made in October and the events over the subsequent months that saw Russia influence the American democratic process prove the dangers of state-sponsored cyber crimes.
There has also been a string of high profile attacks across Europe that has seen the Germany Parliamentary Channel and the French television channel TV5 Monde both shut down – attacks orchestrated by the Kremlin, according to investigators. France and Germany have also warned of the possibility of Russian interference in their elections this year.
British secretary of defence, Sir Michael Fallon, said about Russia: “today we see a country that in weaponising misinformation has created what we might now see as the post-truth age. Part of that is the use of cyber weaponry to disrupt critical infrastructure and disable democratic machinery.”
But it is not just an existential threat to democracy that concerns government and businesses. In 2007, an attack on Estonia saw websites belonging to parliament, banks, ministries, media and broadcasters all shut down. In 2015 a power station in Ukraine was taken offline by a cyber attack leaving 225,000 without power during winter. The effects of banks being shut down to the economy are obvious. The idea of electricity grids, air traffic control or water systems being shut down is terrifying.
Whether from sabotage or espionage, cyber crime costs businesses £365 billion annually. China is one of the five cyber superpowers (along with America, Russia, the UK and Israel) and there have been accusations from a number of countries of Chinese attacks on intelligence materials. However, much of China’s resources have been spent on sourcing international intellectual property. Defence contractors, including Lockheed Martin and NASA, are thought to have been victims of attacks that have originated from China and Chinese telecoms company Huawei has failed in its bid to win contracts in the USA due to security concerns.
“China will be using [cyber technology] as a theatre of relations with other nations, they will be using this as a theatre of economic advantage, and they will be using it as a theatre of war, just as everybody else is,” says Lord Paddy Ashdown, former leader of the Liberal Democrats and senior advisor to cyber security firm G3.
China has its own concerns over cyber security and has just launched a new cyber security law. “Essentially the law requires foreign technology companies to disclose source code and other commercial secrets,” explains Kirk Wilson, CBBC’s executive director. The law, which will be implemented in June, says that all network transmissions must be monitored and all “important” business data must be stored on Mainland Chinese storage devices. Essentially this gives Beijing access to foreign companies’ technology. It also states that no company can use the internet to endanger national security, promote terrorism, or spread false information to disturb the economic order – wording that is very much open to interpretation. If any wrong-doing is suspected the law states that companies must also give government investigators full access to their data.
The American Chamber of Commerce in China issued a statement saying that the new law will do little to protect security of digital systems but will be a barrier to trade and innovation. With foreign companies being required to store data locally in China and only employing technology that is deemed secure, it will, according to the Chamber, give locals an advantage over foreign rivals.
Chinese digital companies are aware that survival relies on providing the government access to their data. WeChat is the latest Chinese company that reportedly allows the authorities to monitor messages. And while emails and digital messages are routinely monitored in other countries, as Lord Ashdown points out, the UK is “necessarily restrained in our activity by the rule of law. Other nations and China would be one, would not be so scrupulous about this.”
So who might be at risk from cyber crime and why? “If you are in or anywhere near to the defence area you are going to find yourself a subject of [an attack] as you would anywhere else,” Ashdown says.
“I advise a small business that makes power tools. Are they going to be the result of state sponsored intervention? One would have thought not – they would be too far below the radar for that,” says Ashdown, “But on the other hand, it is relatively cheap to have private means to do that so you shouldn’t assume anything you do is going to be beyond the reach of the state or private investigators.”
Hackers might be working for political reasons, money or simply just the challenge of it, but hacking technology is simpler to use and cheaper to obtain than ever before. “Previously the scale and technical knowledge needed to operate such attacks was a barrier but this is no longer the case,” says CBBC’s Wilson.
Additional reporting by Nancy Pellegrini